Two-factor Authentication with Google Authenticator
Max Maischein
Frankfurt.pm
Overview
-
What is Two-factor Authentication ("2-FA")
-
Authentication Workflow
-
Demo
-
Security considerations
Who am I?
-
Max Maischein
-
CPAN/PAUSE: CORION
-
DZ BANK Frankfurt
-
Informationsmanagement TxB
Authentication is hard
-
Who gets access?
-
Everybody
-
Passwords
-
SSL-Certificates
-
...
Three Identification Items
You are identified by something you
-
Know (Password)
-
Have (Item)
-
Are (Fingerprint)
A Password ist not enough
-
Keyboard sniffer
-
Passwords get shared
-
Monthly Password Change
-
Weak passwords
-
One-time Pads
-
More convenient: Automatic Password Change
(Secondary) password approaches
-
Real One Time Pad (Codebook, "iTan")
-
Secondary channel (SMS to Mobile, "mTan")
-
Generate Pass-Code dynamically (RSA Token, YubiKey, Battle.Net Authenticator (WoW), ...)
Google Authenticator

-
(Mobile) device as Physical Token
-
Also available for iDevices
-
Initiative for Open Authentication
-
TOTP algorithm, RFC 6238
-
No network connection used
-
"Google Authenticator" app in Google Play Store
-
http://www.dynalogin.org - compatible alternative
How does TOTP work?
-
UTC is the same around the globe
-
Secret + UTC = Code
How does TOTP work?
-
UTC is the same around the globe
-
Secret + UTC = Code
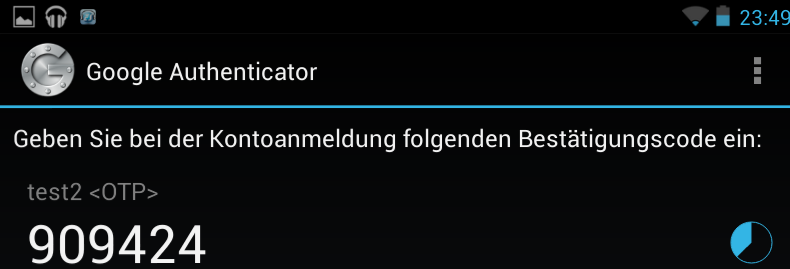
How does TOTP work?
-
UTC is the same around the globe
-
Secret + UTC = Code
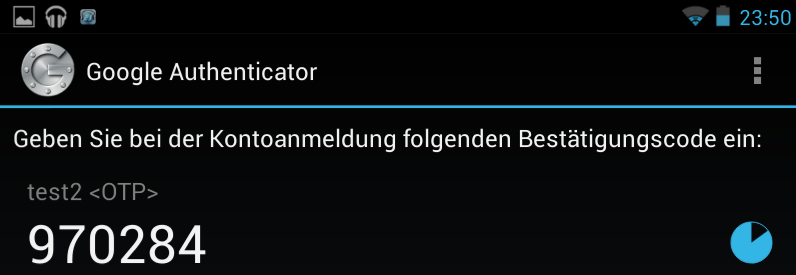
How does TOTP work?
-
UTC is the same around the globe
-
Secret + UTC = Code
-
Everybody who knows the secret can generate the Code!

Workflow
-
Log on with password
-
Set up two-factor authentication ("2-FA")
-
... later ...
-
Log on with password and mobile phone
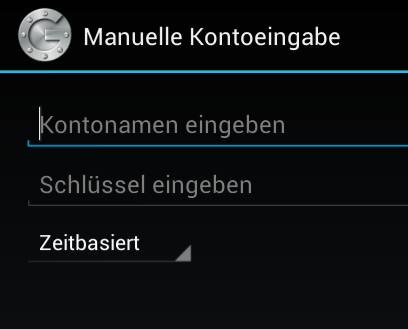
OATH User Experience
-
Setup needs to be easy
-
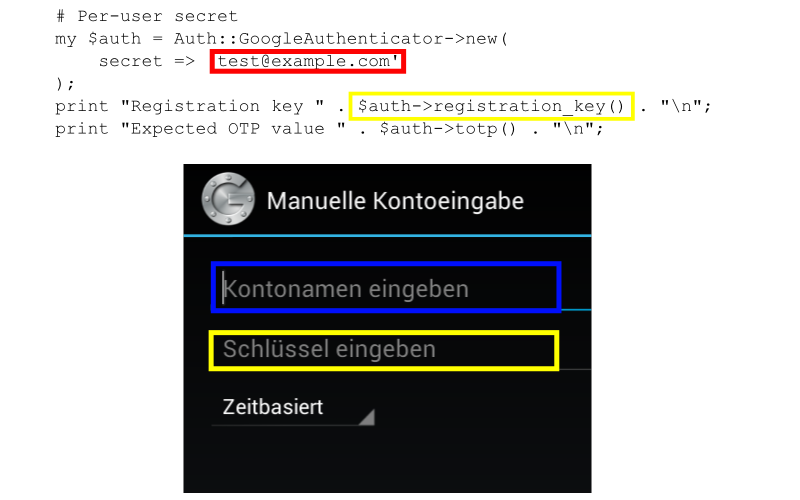
Manual entry of Shared Secret
-
Long base32 strings (RFC 3548)
-
Example:
oyztamdsmjtwymtr
OATH User Experience
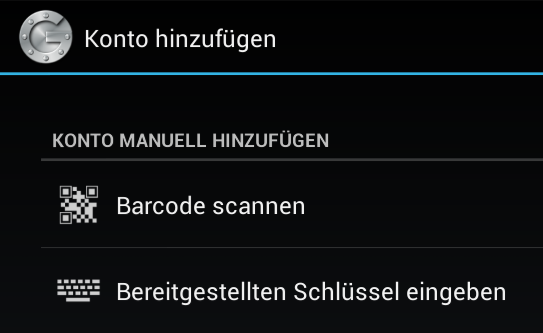
-
Setup needs to be easy
-
Manual entry of Shared Secret
Setup with Google Authenticator
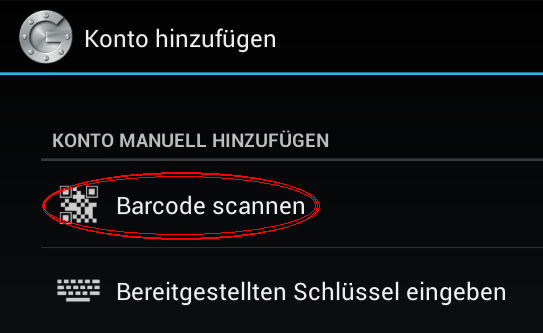
Easier with QRCode
Setup with Google Authenticator

Easier with QRCode
CPAN has our back.

Live Demo
API
1: # Per-user secret 2: my $auth = Auth::GoogleAuthenticator->new( 3: secret => 'test@example.com' 4: );
API
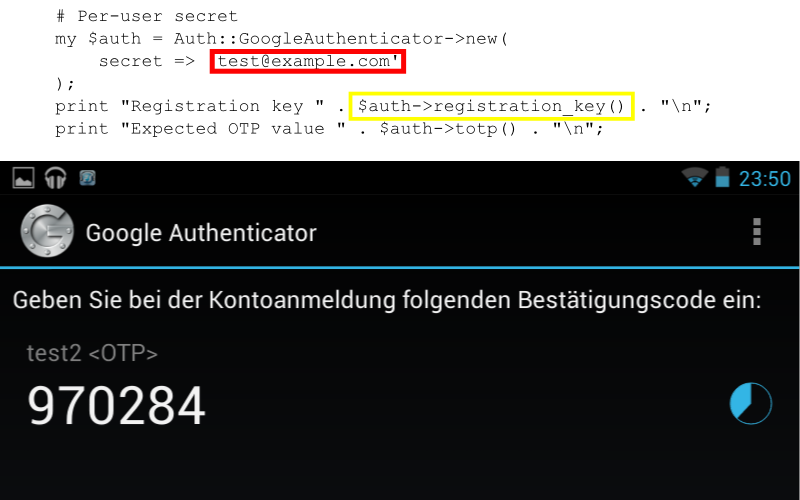
1: # Per-user secret 2: my $auth = Auth::GoogleAuthenticator->new( 3: secret => 'test@example.com' 4: ); 5: print "Registration key " . $auth->registration_key() . "\n";
API
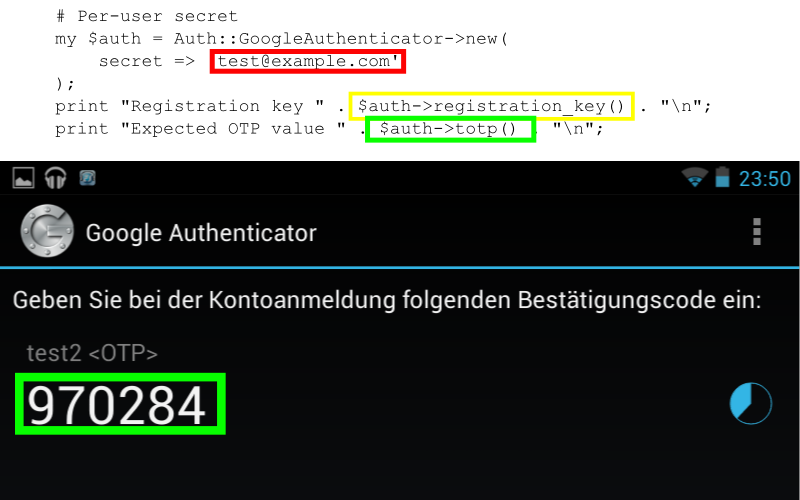
1: # Per-user secret 2: my $auth = Auth::GoogleAuthenticator->new( 3: secret => 'test@example.com' 4: ); 5: print "Registration key " . $auth->registration_key() . "\n"; 6: print "Expected OTP value " . $auth->totp() . "\n";
API
1: # Per-user secret 2: my $auth = Auth::GoogleAuthenticator->new( 3: secret => 'test@example.com' 4: ); 5: print "Registration key " . $auth->registration_key() . "\n"; 6: print "Expected OTP value " . $auth->totp() . "\n"; 7: 8: my $verified = $auth->verify( $user_input ) 9: ? 'verified' 10: : 'not verified'; 11: print "$verified\n";
Demo
API / Application
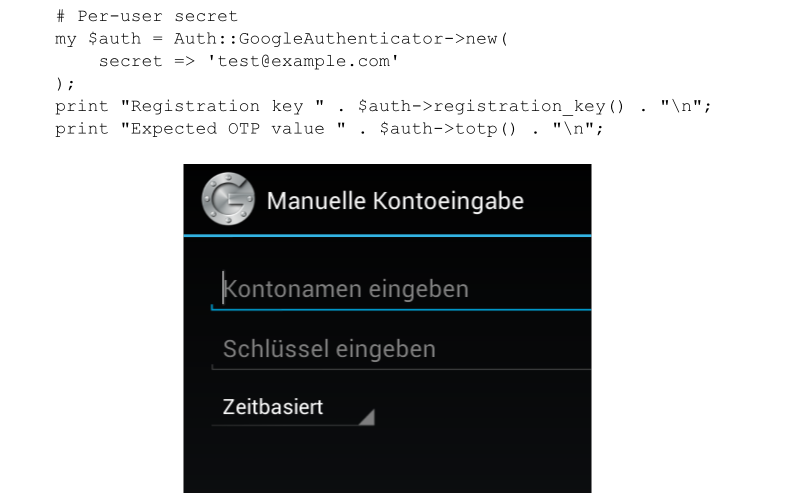
API / Application
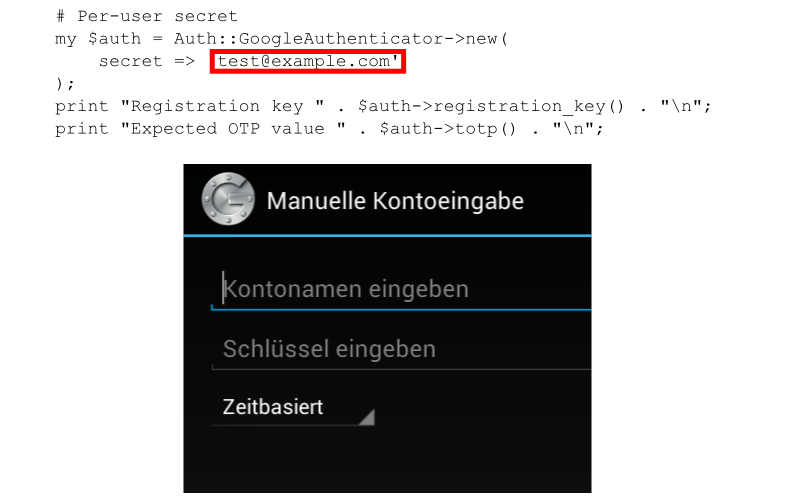
API / Application
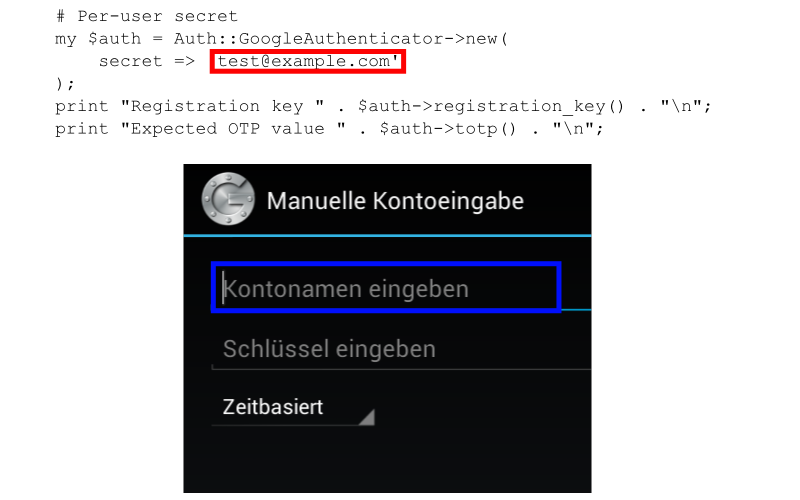
API / Application
API / Application
API / Application
API
1: ->registration_url( $label, $type )
Generates the otpauth:// URL
API
1: ->registration_url( "test2 <OTP>" )
Generates the otpauth:// URL
1: my $au=Auth::GoogleAuthenticator->new(
2: secret=>'test@example.com'
3: );
4: print $au->registration_url('test2 <OTP>')
API
1: ->registration_url( "test2 <OTP>" )
Generates the otpauth:// URL
1: my $au=Auth::GoogleAuthenticator->new(
2: secret=>'test@example.com'
3: );
4: print $au->registration_url('test2 <OTP>')
5:
6: otpauth://totp/test2 <OTP>?secret=orsxg5camv4gc3lqnrss4y3pnu
API
1: ->registration_url( "test2 <OTP>" )
Generates the otpauth:// URL
1: print $au->registration_url('test2 <OTP>')
2:
3: otpauth://totp/test2 <OTP>?secret=orsxg5camv4gc3lqnrss4y3pnu

Security implications
-
Secret is password-equivalent
-
no hashing possible
-
RFC 6238 has no handling advice for the secret!
-
Secret-change is easy
-
Always use a second mechanism!
-
time limit for Two-Factor Sessions
Better security through combination
1: Password TOTP 2-FA
Better security through combination
1: Password TOTP 2-FA 2: 3: Change
Better security through combination
1: Password TOTP 2-FA 2: 3: Change medium
Better security through combination
1: Password TOTP 2-FA 2: 3: Change medium easy
Better security through combination
1: Password TOTP 2-FA 2: 3: Change medium easy easy
Better security through combination
1: Password TOTP 2-FA 2: 3: Change medium easy easy 4: 5: Data leak 6: attack
Better security through combination
1: Password TOTP 2-FA 2: 3: Change medium easy easy 4: 5: Data leak hard 6: attack (bcrypt)
Better security through combination
1: Password TOTP 2-FA 2: 3: Change medium easy easy 4: 5: Data leak hard trivial 6: attack (bcrypt)
Better security through combination
1: Password TOTP 2-FA 2: 3: Change medium easy easy 4: 5: Data leak hard trivial hard 6: attack (bcrypt)
The weakest link
-
Google - "Password-protocols" (IMAP, POP3, ...) circumvent 2-FA
-
EverNote - direct links to files circumvent 2-FA
-
Authy.com - Synchronizes your tokens with their server
-
...
Moving to two-factor authentication
-
Change ALL access (Google!)
-
Store shared secret encrypted on disk, decrypt only in memory
-
Password reset / lost mobile phone?!
-
Idea: 3 master-reset passwords for printing (PUK)
Relevant Modules
Auth::GoogleAuthenticator uses
Authen::OATH
Imager::QRCode
Dancer
Sample code
"Google Authenticator" in Google Play Store
http://code.google.com/p/google-authenticator/
Available for iDevices
Sample code and module is online on CPAN in
Auth::GoogleAuthenticator
http://www.dynalogin.org - another Android Soft-Token
Thank you!
"Google Authenticator" in Google Play Store
http://code.google.com/p/google-authenticator/
Available for iDevices
Sample code and module is online on CPAN in
Auth::GoogleAuthenticator
http://www.dynalogin.org - another Android Soft-Token
Questions?
Max Maischein (corion@cpan.org)